Balance theory manages security investment events end-to-end. Detect investment decision triggers, run each event for the best cost and coverage outcome, and continuously rationalize the program to maximize the impact of every dollar deployed.

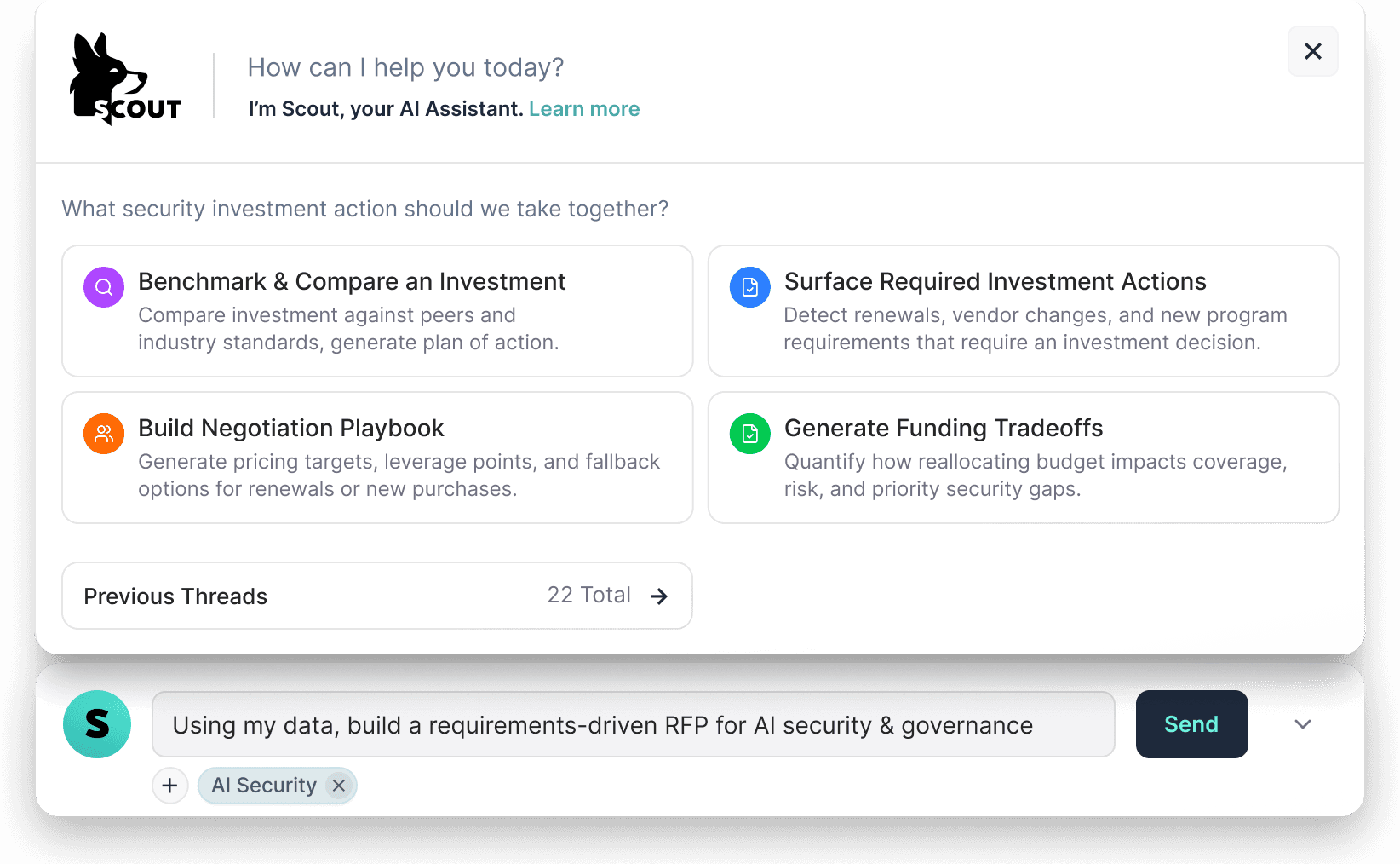
Meet Scout: Your Cyber Strategy & Spend Co-Pilot.
Scout isn't just an assistant. It's your portfolio manager, negotiator, and strategist, combining intelligence retrieval with embedded agents that can take action per your instructions.
How Security Budget Owners Use Balance Theory
Outcomes, Not Features

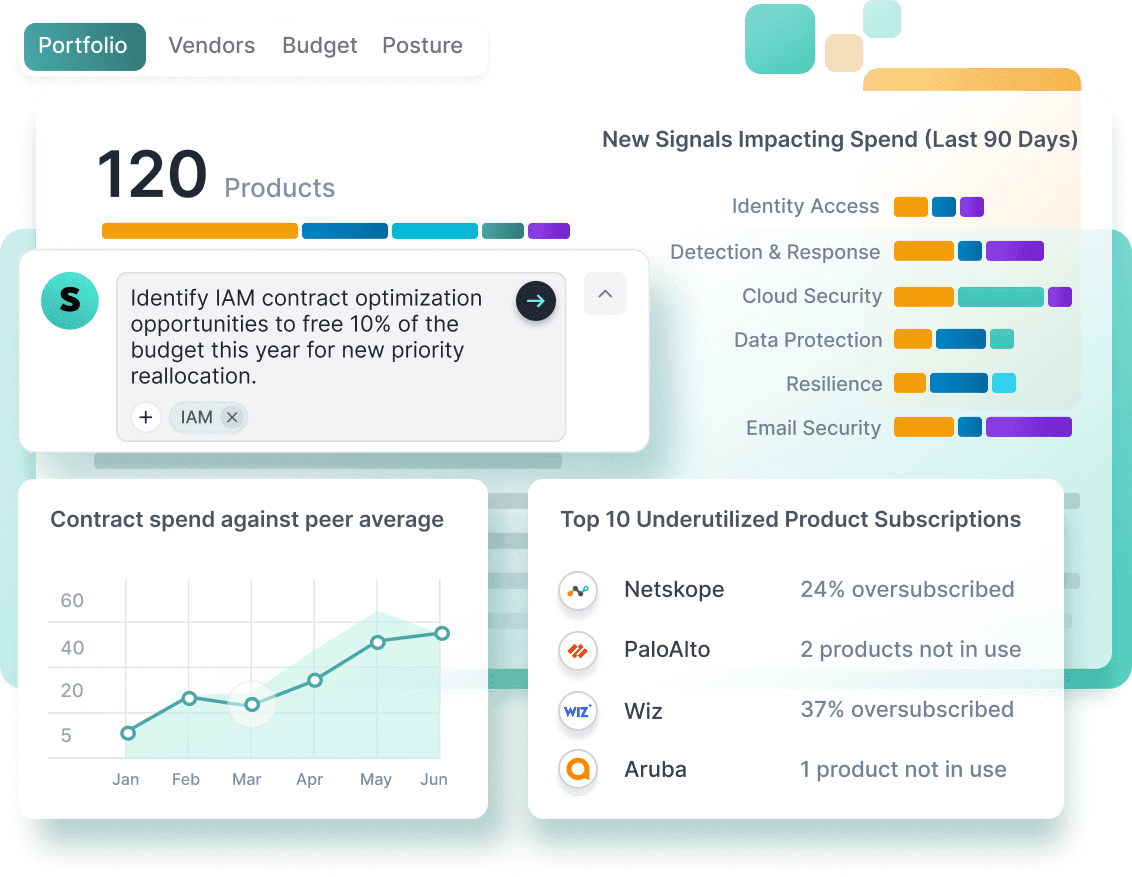
Return wasted dollars back to your budget.
Reallocate wasted spend into the gaps keeping you up at night.
Shrink solution time from 6 months to 6 weeks.
From need → vendor evaluation → trade-offs → executed buy.
Get to better vendor pricing overnight.
Leverage real benchmarks and AI-generated negotiation briefs.
Map against every major framework in minutes.
Expose overlaps, gaps, and compliance coverage instantly.

Walk into the boardroom with answers.
AI-generated reports you can stand behind.
Unlock your Security Strategy & Budget Co-Pilot
Domain Intelligence. Agentic Workflows. Transaction Network. 24/7 Support.